Show some ❤️ by starring this Article!
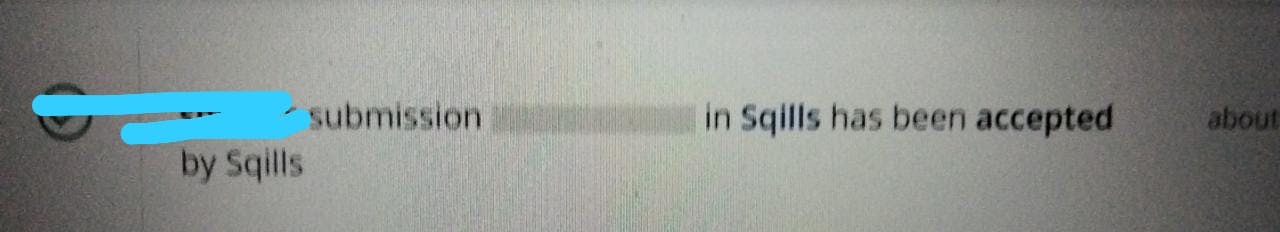
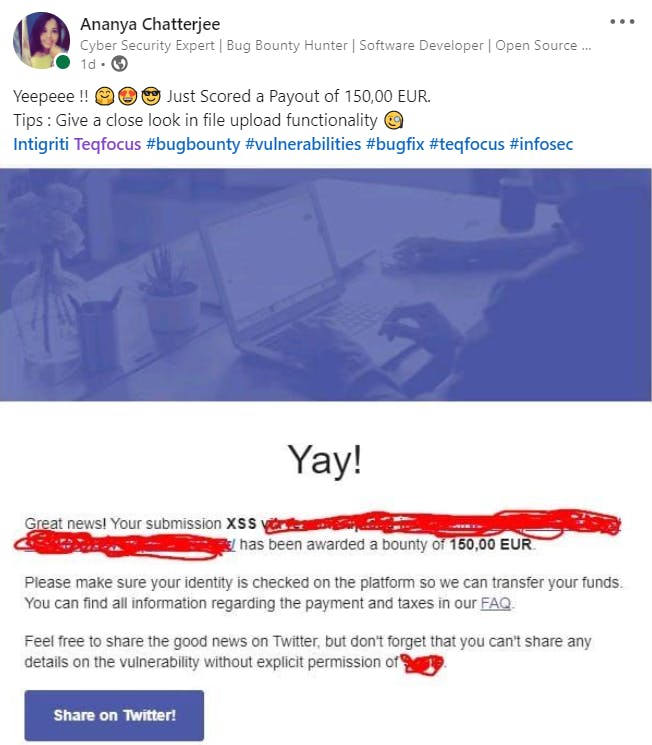
Hey Hackers , I hope you all are doing great in your life and if not, then you are at the right place to at least remove the queries of XSS from your life. This is my 8th Valid Bug on Intigriti. I was rewarded 150,00 EUR by Sqills.
 This article is going to make you somewhere close to perfection (as we all know nobody is perfect :P). So, without wasting any time let’s take a dive into this.
This article is going to make you somewhere close to perfection (as we all know nobody is perfect :P). So, without wasting any time let’s take a dive into this.
What is XSS ( cross site scripting )
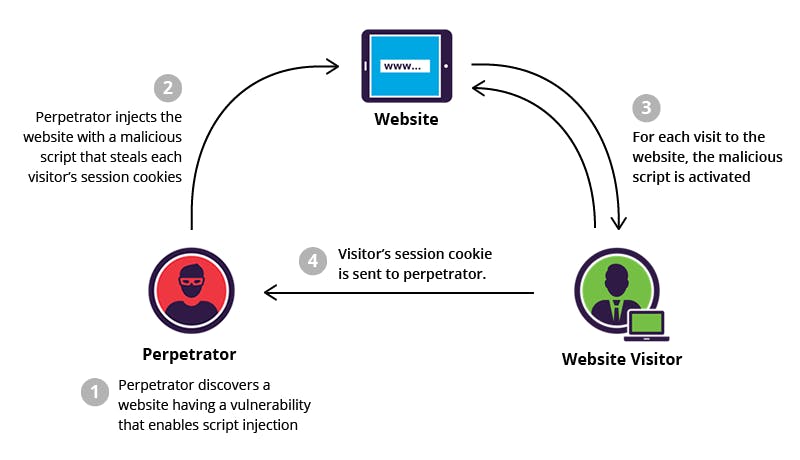
XSS is a Client Side Code Injection attack. With that I mean, by embedding malicious code in a genuine web page, the attacker hopes to execute harmful scripts on the victim’s web browser. I found this image to be helpful to understand the concept clearly. Have a look and try to understand what is actually happening?
XSS is a very interesting and dynamic bug class for a number of reasons.
- The severity can range anywhere from informative to critical, depending on the application and context
- It can result in remote command execution in some contexts
- Due to the dynamic nature of the bug class, it’s difficult to prevent against from a development standpoint
- More complex XSS vulnerabilities will be mostly missed by automated tooling
Still having Doubt?? Let's Connect virtually on Whatsapp & Instagram
Gaining an XSS on a vulnerable application may give an attacker the ability to:
- Steal session tokens, giving them full control of the user’s session
- Bypass Same Origin Policy (SOP), allowing them to perform sensitive actions as if they were logged the victim user
- Exfiltrate information that is viewable by the victim user, for example
The Vulnerability
I can't share any details on the vulnerability, though I' don't have permission. But here is the example :
The backend code might look something like this:
<html>
<head><title>MyApp</title></head>
<body>
<?php
$name = $_GET['name'];
if (strpos($name, 'script') !== false) {
http_response_code(403);
die('Forbidden');
}
?>
Welcome to MyApp, <?php echo $_GET['name']; ?>
</body>
</html>
Now, if we try to inject , it won’t work:
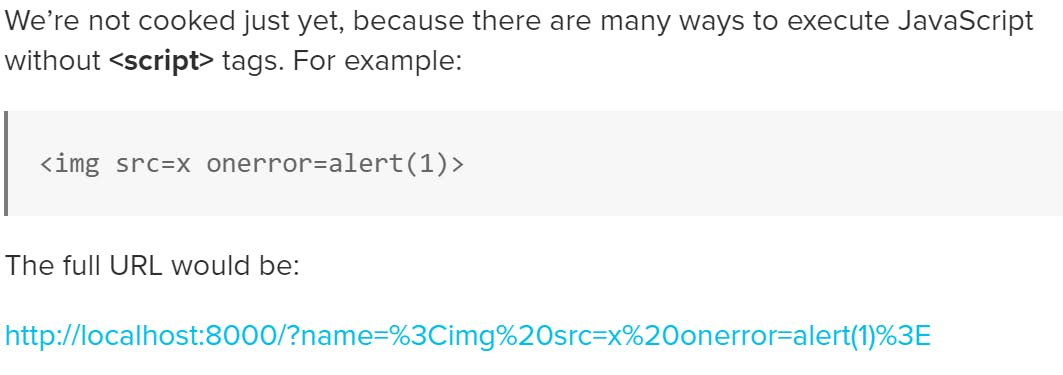
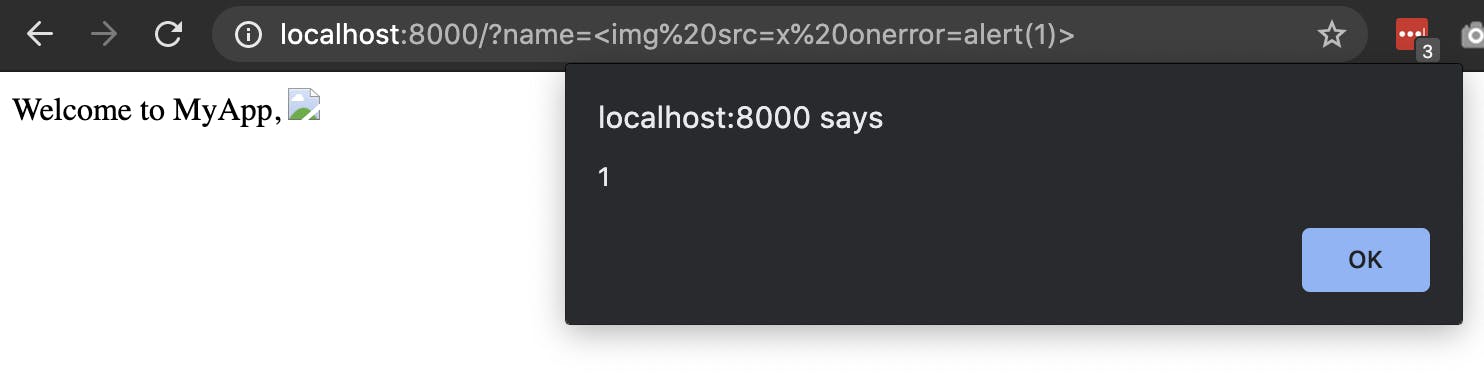
In this case, we’ve used a handy little feature called HTML Event Attributes. They allow you to specify JavaScript to execute when a specific event occurs. In this case, we have attempted to load an image with the src attribute set to “x”. Of course, there is no image hosted at “x”, so an error occurs. When an error occurs, the onerror Event attribute is fired, which we set to be alert(1). A good list of event attributes can be found here: https://www.w3schools.com/tags/ref_eventattributes.asp
ALERT IS BLOCKED
Another common blacklisted word is “alert”, which can be bypassed easily by using prompt(1), console.log(1), or literally anything else.
Strings are blocked
Sometimes you will run into situations where you can not form a string, maybe because quotes are blocked, or some other reason. In this case, String.fromCharCode can be really handy. It takes ASCII codes, and then turns them into a string, for example this payload:
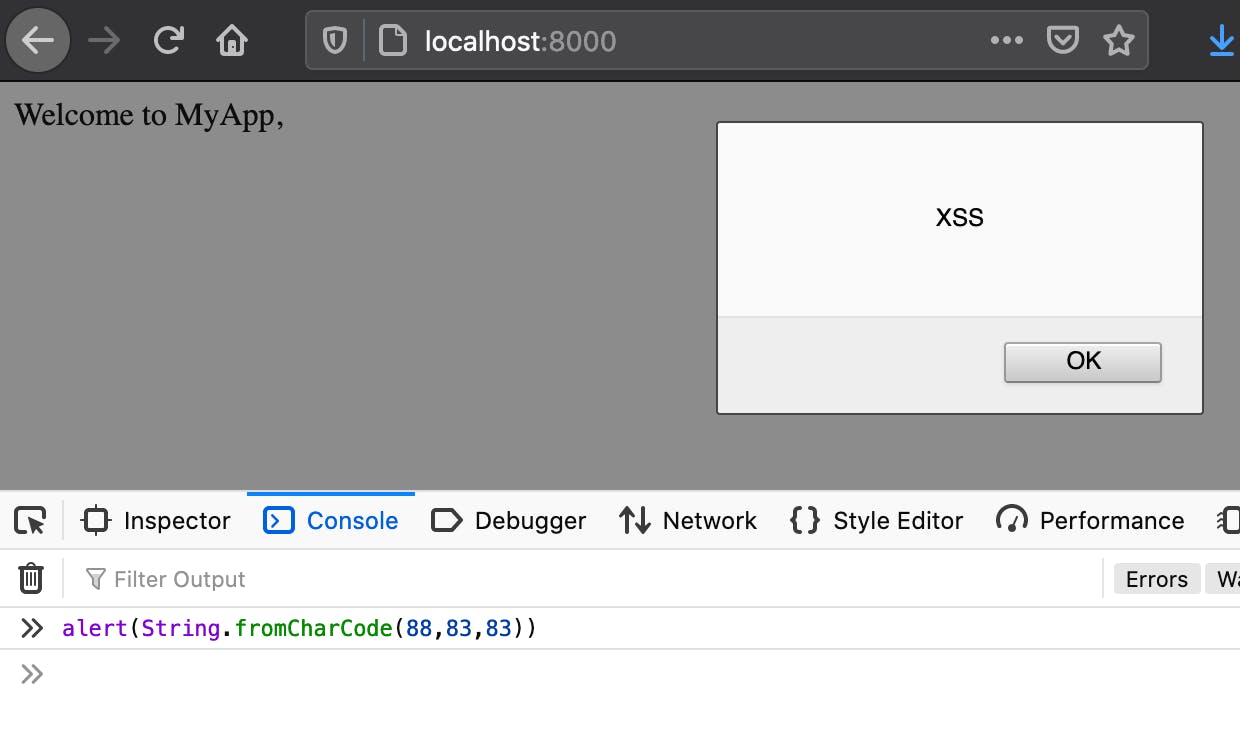
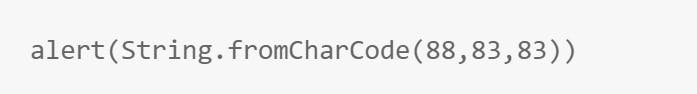 Will create an alert box with the characters corresponding to 88, 83 and 83. Which just happens to be XSS:
Will create an alert box with the characters corresponding to 88, 83 and 83. Which just happens to be XSS:
 If you enjoyed this story, please click the 👏 button and share to help others find it! Feel free to leave a comment below. Thankyou Hashnode
If you enjoyed this story, please click the 👏 button and share to help others find it! Feel free to leave a comment below. Thankyou Hashnode

